A subgroup of Sandworm, sometimes referenced under names like “BadPilot” or “Seashell Blizzard”, was exposed in 2025 for a global credential-theft and intrusion campaign. The group, linked to Russia’s GRU military intelligence, exploited multiple vulnerabilities to infiltrate organisations across critical sectors: energy, oil and gas, telecommunications, shipping, arms manufacturing, and various governments worldwide, dating back to at least 2021.
After intrusion, they executed credential theft, lateral movement, persistence, and post-compromise activities, allowing them to maintain long-term access to sensitive systems.
Phishing Evolution


Phishing has traditionally relied on two main outcomes, credential theft through fake login pages, and malware delivery through malicious attachments. In 2024 and 2025, this model shifted in a significant way, with the rise of user executed command phishing, most notably through ClickFix and its successor FileFix. This represents a fundamental change in how phishing achieves initial access, moving from persuading users to open files to persuading them to run commands themselves.
The ClickFix model began to emerge at scale, in late 2024, as attackers started using highly convincing fake web pages that impersonated browser security checks, Windows updates, CAPTCHA challenges and cloud verification portals. Instead of prompting a file download, these pages instruct the victim to open Run, PowerShell or a terminal, and paste a command shown on screen. That single command then retrieves and executes malware directly in memory. From a phishing perspective, this removed the most heavily monitored stage of the attack chain - which had previously been the malicious attachment.
During 2025, this method became one of the fastest growing phishing delivery techniques. Industry reporting showed a several hundred per cent growth in ClickFix style campaigns within a matter of months. What began as a technique largely used to deploy infostealers quickly evolved into a common delivery mechanism for remote access tools, loaders and early-stage ransomware components. At the same time, the phishing pages themselves became far more sophisticated, including OS aware scripting, with different commands for different platforms, automatic copying of commands to the clipboard, video walkthroughs, full screen fake security overlays, and lures themed around Microsoft, Google, Zoom, internal IT portals and document sharing platforms.
At this point, phishing no longer needed to overcome endpoint controls directly. Instead, the success of the attack depended on persuading the user to carry out the execution step voluntarily.
This trend developed further in 2025 with the appearance of FileFix, which extends the same social engineering principle into the Windows File Explorer address bar. Victims are instructed through phishing pages or messages to paste what appears to be a harmless file path into Explorer. In reality, it’s a crafted PowerShell command that executes immediately. Unlike early ClickFix campaigns, which were largely associated with infostealers, FileFix has already been linked directly to active ransomware operations. This makes it a clear bridge between phishing and full network compromise.
Together, ClickFix and FileFix demonstrate a broader transformation in phishing. The technique has shifted from attachments to instructions, from technical exploitation to behavioural control, from low-level malware to ransomware access operations, and from isolated tricks to standardised phishing workflows that can be reused across multiple threat groups.
By the end of 2025, phishing is no longer defined primarily by fake logins and weaponised attachments. It has evolved into a browser-driven execution channel, where the website becomes the launcher and the victim becomes the installer. This evolution fundamentally changes how phishing must be detected, trained against and disrupted, shifting the defensive focus away from files and emails and towards user behaviour, browser trust decisions and command line execution controls.
The 2025 Global Surge in Mobile Banking Malware and Crypto-Phishing Attacks (Financial Cyber-Threat Trend)
According to security firms’ 2025 reports, banking-trojan incidents targeting mobile devices increased more than 3.6 times compared to the previous year, while phishing attacks focused on cryptocurrencies grew by around 83%.
Malware such as ToxicPanda emerged, targeting users in Europe and beyond, abusing Android accessibility services to hijack banking and crypto credentials, bypassing conventional protections.
Relevance: Rather than a single “big breach” this reflects a systemic trend, a shift in cyber-financial crime toward mobile devices and crypto, affecting vast numbers of potential victims worldwide.
https://thehackernews.com/2025/02/bybit-confirms-record-breaking-146.html
Major Cloud-Infrastructure and Supply Chain Attacks Targeting Critical Systems (APT plus Supply Chain Threat Vectors)
The 2025 threat landscape has underscored a growing danger: state-sponsored and criminal groups increasingly exploit software supply chains, cloud misconfigurations, and third party vulnerabilities to gain access to high-value environments (energy, telecoms, manufacturing, etc.).
These attacks are often multi-staged: an initial compromise via exposed services or third party tools, followed by credential theft, lateral movement, and deployment of backdoors or wipers (particularly in geopolitical conflict zones, e.g. related to Russia-Ukraine).
Relevance: This highlights that, for 2025, the most dangerous threats weren’t always “loud” breaches but were often hidden supply chain compromises that can stay undetected for months while posing a massive risk to national security and critical infrastructure.
https://www.theregister.com/2025/02/12/russias_sandworm_caught_stealing_credentials
https://www.microsoft.com/en-us/security/blog/2025/03/05/silk-typhoon-targeting-it-supply-chain/
Ransomware Increasingly Targeting the Supply Chain
Analysis of ransomware victim data shows a clear structural shift between 2024 and 2025, moving from predominantly isolated organisational compromise to deliberate supply chain and multi-tenant targeting.
In 2024, ransomware activity was characterised by high global volume but largely individual victim targeting. Although multiple victims were sometimes posted within short time windows, these typically:
- Spanned different sectors and countries.
- Showed no consistent shared service provider.
- Reflected opportunistic endpoint compromise, rather than upstream platform breaches.
Even where infostealer data appeared, it was used mainly for credential resale, not as a widespread propagation layer for ransomware operations. True supply chain incidents existed, but they were the exception rather than the rule.
By contrast, 2025 shows a marked operational evolution towards platform-driven compromise and sector-wide exposure.
The data demonstrates:
- Same-sector, same-region victim clusters, disclosed by a single ransomware group, within short time windows.
- Strong indicators of compromise at the level of managed service providers, SaaS platforms, shared CRMs and BPO systems.
- The systematic reuse of large infostealer datasets as secondary credential supply chains, into cloud, payroll, finance and SaaS platforms.
- Campaign branding and batch disclosures that explicitly signal ecosystem-level rather than single-entity compromise.
UAE Real Estate Sector
More than ten real estate brokerages across the UAE were listed by a single ransomware group within minutes of each other. This strongly indicates a breach of a shared upstream IT provider, property CRM or multi-tenant SaaS platform, rather than ten independent intrusions.
South Korean Private Equity and Asset Management Sector
In another major 2025 supply chain incident, a large number of South Korean private equity funds and asset managers were exposed under a single coordinated ransomware campaign.
Public reporting confirms that:
- The initial breach occurred at the level of a cloud server operated by an IT subcontractor or managed service provider.
- Dozens of downstream PE and asset management firms were impacted as a result.
- Data was leaked in planned stages under a shared campaign identity.
This case is particularly significant because private equity firms act as risk multipliers. A single upstream compromise exposes not only the management firm itself, but also investors, portfolio companies, law firms, fund administrators and custodians, extending supply chain impact far beyond the original victim list.
Single ransom disclosures in 2025 have increasingly contained data for multiple unrelated companies, indicating compromise of shared hosting, file transfer or backup providers, rather than direct compromise of each named organisation.
Payroll platforms, call centres and supply chain software vendors increasingly appear as primary victims, exposing entire client portfolios rather than single corporate environments.
The comparison shows that:
- 2024 prioritised breadth of victims.
- 2025 prioritised leverage through shared platforms.
In 2024, ransomware groups largely operated by compromising individual networks at scale. In 2025, the dominant model increasingly involves compromising one provider to reach many downstream victims simultaneously.
- Supply chain exposure is now a primary ransomware risk, not a secondary concern.
- Smaller organisations are increasingly impacted indirectly via vendors, even where their own perimeter controls remain strong.
- Infostealers now act as credential distribution infrastructure, accelerating ransomware access across third party ecosystems.
- Sector-wide disruption is becoming operationally normal, particularly in:
- Financial services and private equity.
- Real estate and property services.
- Manufacturing and engineering.
- Professional services.
- Outsourced business and payroll platforms.
Social Engineering: Humans Continue to be the Weakest Link
In 2025, social engineering moved beyond short-lived phishing and pretexting into persistent, persona-driven trust exploitation. Threat actors increasingly invested in building credible digital identities, maintaining long-term contact with targets and operating inside trusted networks before attempting technical compromise.
Where earlier social engineering relied on urgency and deception alone, 2025 saw a shift towards relationship-based intrusion, with attackers behaving more like recruiters, suppliers, consultants, developers and even internal staff.
Threat groups now routinely construct fully formed personas, including:
- Long-standing LinkedIn and GitHub profiles.
- Credible employment histories and endorsements.
- Active participation in industry forums, conferences and developer communities.
- Consistent language use, time-zone realism and behavioural patterns.
These personas are not disposable. They are maintained for months, sometimes years, and are used to engage targets gradually through professional networking, collaboration offers or recruitment approaches.
Lazarus and the Operationalisation of Trust
In 2025, the Lazarus Group continued to refine its employment and recruitment-themed tradecraft, targeting:
- Software developers.
- Blockchain engineers.
- Cyber security researchers.
- Financial and cryptographic specialists.
- Long technical conversations.
- Code sharing and peer review.
- Fake startup recruitment.
- Investment and partnership discussions.
- Establish professional credibility.
- Move malware delivery into trusted collaboration contexts.
- Bypass many email and web security controls entirely.
Malware is often introduced only after trust is established, embedded into shared projects, interview coding tasks or “private” tools.
Expansion Across the Threat Landscape
This approach is no longer limited to state-linked groups. Throughout 2025, ransomware crews, access brokers and fraud groups also adopted persona-driven social engineering, particularly to:
- Gain access to MSPs and IT administrators.
- Compromise cloud administrators.
- Infiltrate BPOs, payroll providers and customer service platforms.
- Establish supply chain footholds.
- Internal IT staff.
- New suppliers or auditors.
- Legal representatives.
- Mergers and acquisitions advisers.
- HR and recruitment partners.
These approaches are often combined with deep contextual knowledge from prior data breaches, infostealer logs and leaked internal documents, making the social engineering highly personalised.
The Convergence with Browser-Driven Execution
At the same time, 2025 also saw the rise of instruction-based execution techniques, such as ClickFix and FileFix, where attackers persuade victims to run commands themselves.
- Trust replaces exploitation.
- User behaviour replaces technical vulnerability.
- The victim becomes the execution mechanism.
In many campaigns, persona-based engagement is now used to soften the target before directing them to these browser-driven execution flows.
By the end of 2025, social engineering had shifted from:
- Short-form deception to long-term behavioural manipulation.
- Opportunistic phishing to relationship-driven intrusion.
- Impersonation to operational identity theft.
- Technical exploitation to trust exploitation.
This evolution makes traditional awareness training, based purely on spotting obvious phishing indicators, increasingly insufficient. The primary control failure is no longer technical detection but misplaced trust in seemingly legitimate digital relationships.
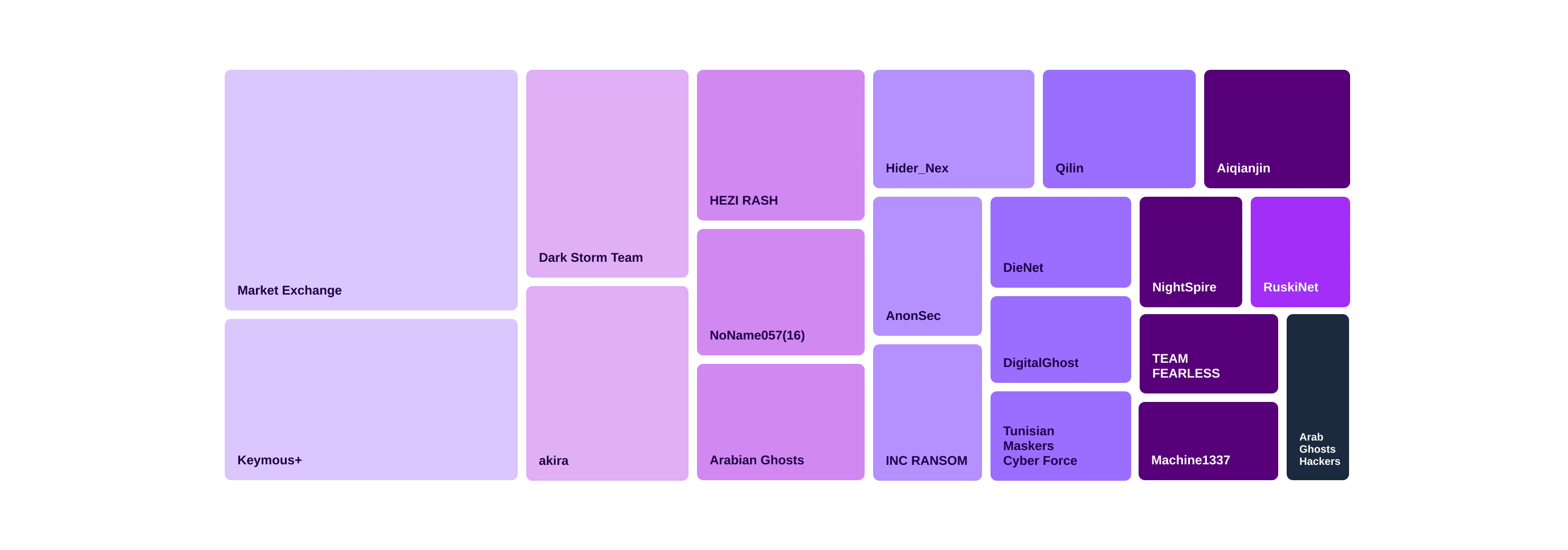
Threat actors targeting financial entities in 2025
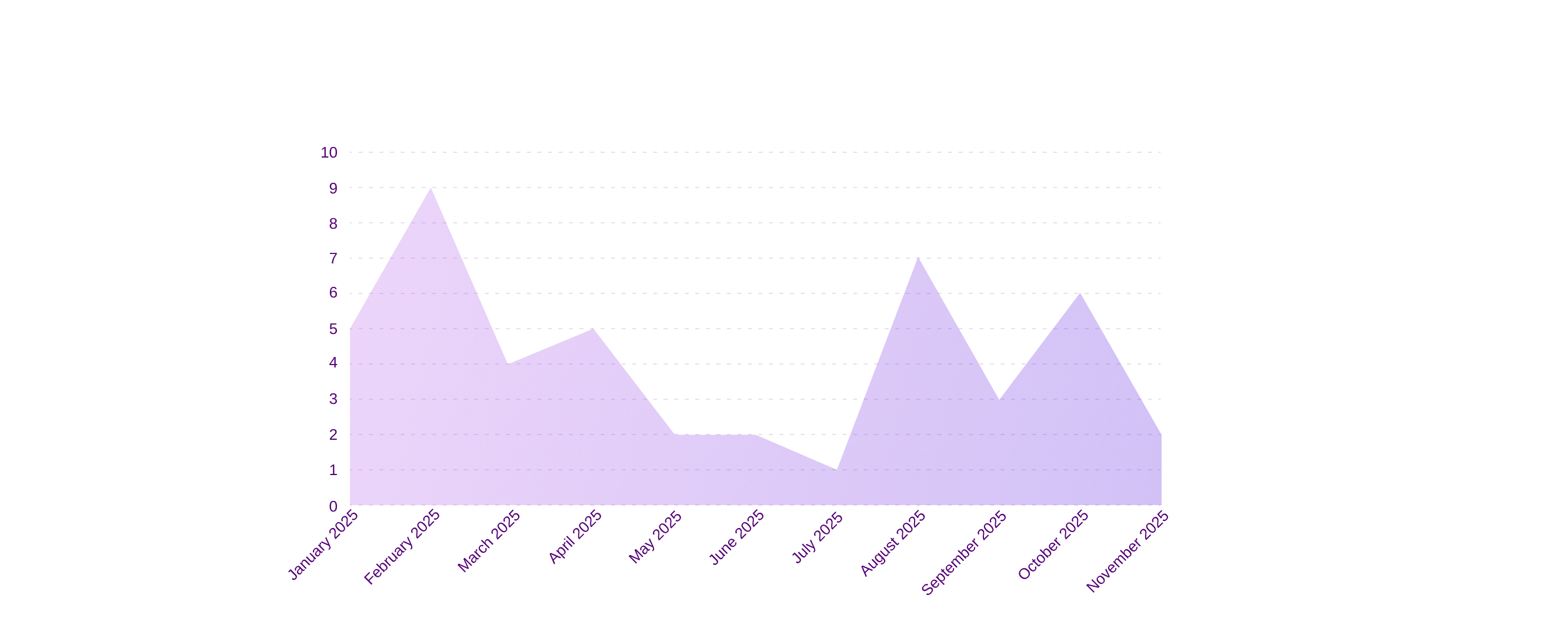
Ransomware vs Finance

Managing Risk of AI Adoption
AI is transforming how organisations across the globe work, from powering internal knowledge hubs and embedding tools like CoPilot in Teams, to generating production-ready code. But every innovation brings new cyber risks, compliance challenges, and attack surfaces. By utilising our AI code testing service, you can ensure your AI deployments are resilient, compliant, and ready for the real world.
Insights

Advanced Malware and Supply Chain Shocks
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

2025 Cyber Round-Up: The Threat Evolution
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

Data Breaches Surge Across All Sectors, Exposing Sensitive Data and Reducing Digital Trust
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

Ransomware Attack Cripples Polish Hospitals, Raising Concerns Over Critical Infrastructure Security
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

